World security vulnerability in this paper we propose a novel proximity-based mechanism for IoT device authentication called Move2Auth for the purpose of enhancing IoT device security. Improper Usage of Authentication or Authorization Mechanisms.

Network Segmentation An Overview Sciencedirect Topics
A client-server-based access control and authentication protocol.
. Weak or default passwords. Authentication Failure Rate configuration allows a security administrator to configure the router to lock itself after 3 unsuccessful login attempts. DIsable port 80 and enable on port 443 and should fix your problem.
Enable inbound vty Telnet sessions. The router is serving as a time source for the device at 19216811. Refer to the exhibit.
As the routers become more and more confused its vulnerability becomes really exposed as the malicious data starts to circulate around the network creating a loop. This means that the Web server allows POST requests via port HTTP80 plain-text form based authentication. Yes of course but you must have at least one point of contact anyway.
Cryptographic algorithm for ISN generation. All systems that are connected to a LAN or the Internet via a modem run services that listen to well-known and not so well-known ports. This proceeds to causing major congestion on the network and makes it extremely difficult for any networking team to debug.
8021x DHCP snooping and Nondefault native VLAN are techniques to mitigate access layer types of vulnerabilities. One router is configured as the NTP master and the other is an NTP client. Hackers are interested in easier targets if they cant break your.
What two statements describe the NTP status of the router. 8021x is a protocol used in port-based authentication. Papertrail makes it easy for one person to make sense of these logs by parsing the logs into tokens and presenting the product usage in an easy-to-use graphical way.
With Basic Authentication the user credentials are sent as cleartext and because HTTPS is not used they are vulnerable to packet sniffing. One or more directories are protected using Basic Authentication over an HTTP connection. Generate the SSH keys.
While WPA2 offers more protection than WPA and therefore provides even more protection than WEP the security of your router heavily depends on the password you set. Authentication scheme based on the client and server supported algorithms and ci- phers when the authentication phase is reached. More possible ISNs in particular time period low probability of successful prediction.
Port Scanning is one of the most popular techniques attackers use to discover services that they can exploit to break into systems. In Move2Auth we require user to hold smartphone and perform one of two hand-gestures moving towards and away and rotating in front of IoT device. The Asustor AS-602T Buffalo TeraStation TS5600D1206 TerraMaster F2-420 Drobo 5N2 Netgear Nighthawk R9000 and TOTOLINK A3002RU.
This can result in a number of vulnerabilities allowing attackers to obtain sensitive user data and potentially bypass authentication completely. Six of them can be remotely exploited without authentication. -Both routers are configured to use NTPv2-Router R1 is the master and R2 is the.
Choose two The router is serving as an authoritative time source. However many web applications content management systems and even database servers are still configured with weak or default passwords. Routers R1 and R2 are connected via a serial link.
Router R1 is the master and R2 is the. Both routers are configured to use NTPv2. After the EAP method is decided.
Using this vulnerability as an attacker can change user profile information change status create a new user on admin behalf etc. Which two pieces of information can be obtained from the partial output of the show ntp associations detail command on R2. OAuth 20 is highly interesting for attackers because it is both extremely common and inherently prone to implementation mistakes.
Authentication and authorization policies should be role-based. Common access layer threats include unauthorized clients connecting to a LAN rogue DHCP servers and VLAN hopping by way of double tagging. Bypass Basic Authentication in Routers.
Earlier we described how one of the key approaches to securing API is authentication and. The router is attached to a stratum 2 device. One router is configured as the NTP master and the other is an NTP client.
Network Security Omission 2. There are four steps to configure SSH support on a Cisco router. Show activity on this post.
Increase the granularity of the increase. Often in IoT devices there are flaws in the implementation of the authorizationauthentication mechanisms. SSH is a protocol used for remote login.
With a server-based method the router accesses a central AAA server using either the Remote Authentication Dial-In User RADIUS or Terminal Access Controller Access Control System TACACS protocol. Use Basic Authentication over an HTTPS connection. In this section well teach you how to identify and exploit some of.
Like any web serverapplication there might be flaws in the source code that cause the interface to be vulnerable to a Cyber based attack. WPA and WPA2 let you use passwords of up to 63 characters. Defense against Sequence Number Prediction.
Increase the rate of change of ISN. Configure the IP domain name on the router. The IP address of the time source for.
Authentication Failure Rate provide a level of protection. Use as many various characters in your WiFi network password as possible. Set the domain name.
Which two pieces of information can be obtained from the partial output of the show ntp associations detail command on R2. A friend bought a router model GN-B46B of Gigabyte and asked me if it is dangerous to expose the router to the WAN. Even if your website redirects you to HTTPS it does not matter as someone can force the request to HTTP.
By integrating Papertrail in your application you can track possible vulnerabilities. The organization publishes a list of top web security vulnerabilities based on the data from various security organizations. Passwords shouldnt even be part of a network security vulnerability discussion knowing what we now know.
Routers R1 and R2 are connected via a serial link. Bad data malicious command. By the way if you cannot access the administrator page the account name is admin and password is.

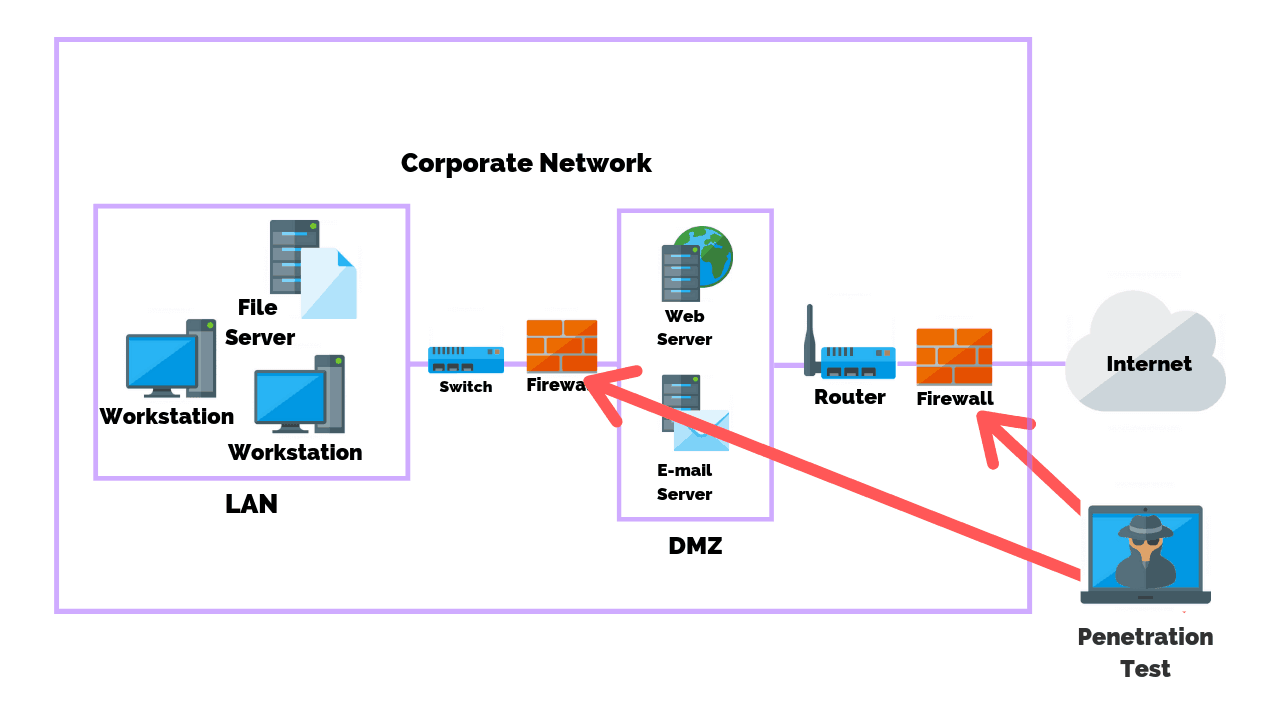
Firewall Penetration Testing Steps Methods Tools Purplesec

Timeline Of Two Stage Attack Against Vulnerable Ios Router Of Unknown Download Scientific Diagram

B Illustrates A Network In Which The Malicious Router X Gray Circle Download Scientific Diagram
0 Comments